Information Security / Cybersecurity & System Availability
Highlight Performance
Data breaches
Total number of clients, customers, and employees affected by the breaches

Management Approach
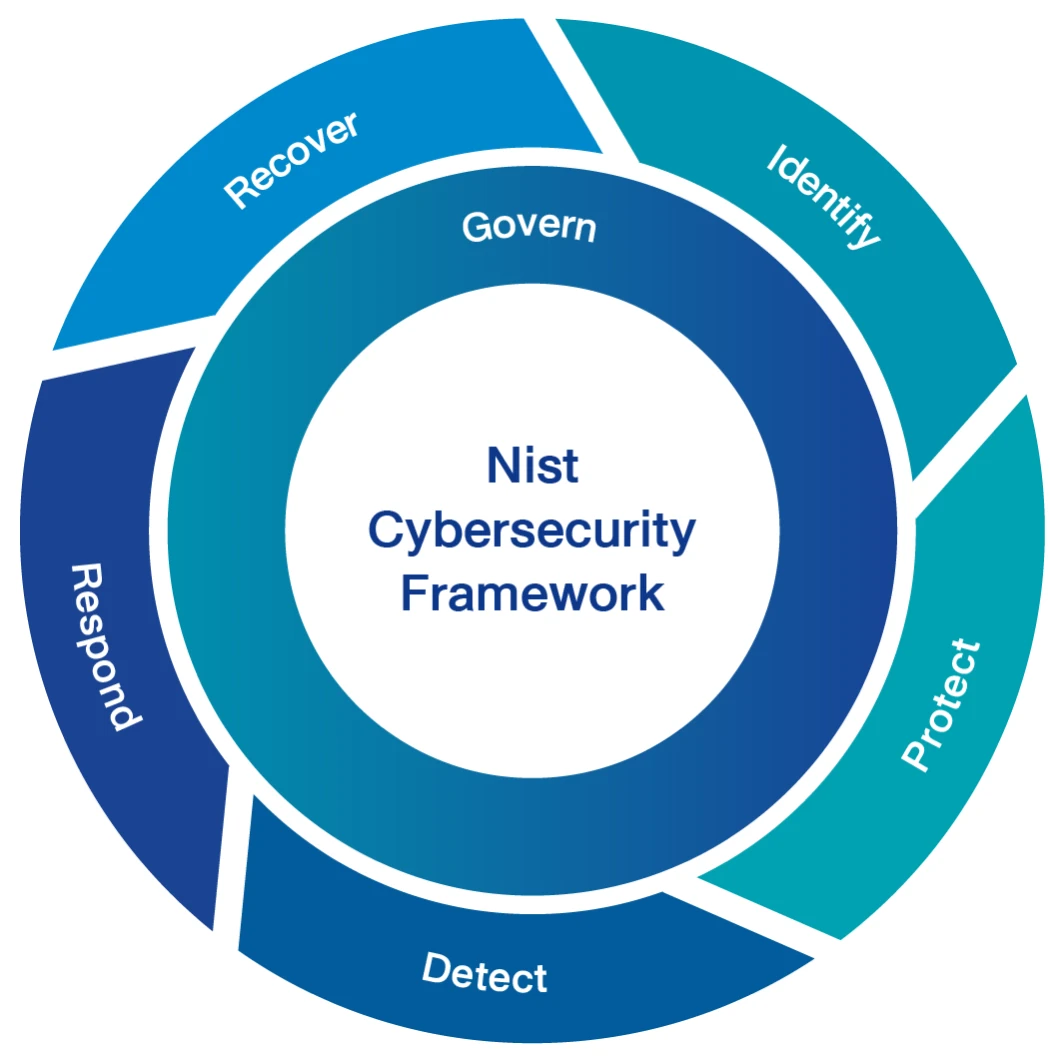
Osotspa recognizes the critical importance of cybersecurity in today's interconnected world and has made it a top priority within its operations. Leveraging the latest NIST Cybersecurity Framework (CSF) 2.0, Osotspa establishes a comprehensive approach to protect its digital assets and maintain the trust of its stakeholders. By integrating the NIST CSF's core functions of Govern, Identify, Protect, Detect, Respond, and Recover, Osotspa ensures a robust cybersecurity strategy that addresses potential threats proactively and ensures swift recovery in case of incidents.
Furthermore, Osotspa goes beyond mere compliance by fostering a culture of cybersecurity awareness and empowerment throughout its workforce. Through continuous training, education, and the implementation of stringent policies, every employee at Osotspa becomes a proactive defender against cyber threats. By embracing cutting-edge technologies and strategic partnerships, Osotspa remains agile and adaptive in an ever-evolving cybersecurity landscape, reaffirming its commitment to safeguarding its operations and maintaining the trust of its customers and partners.
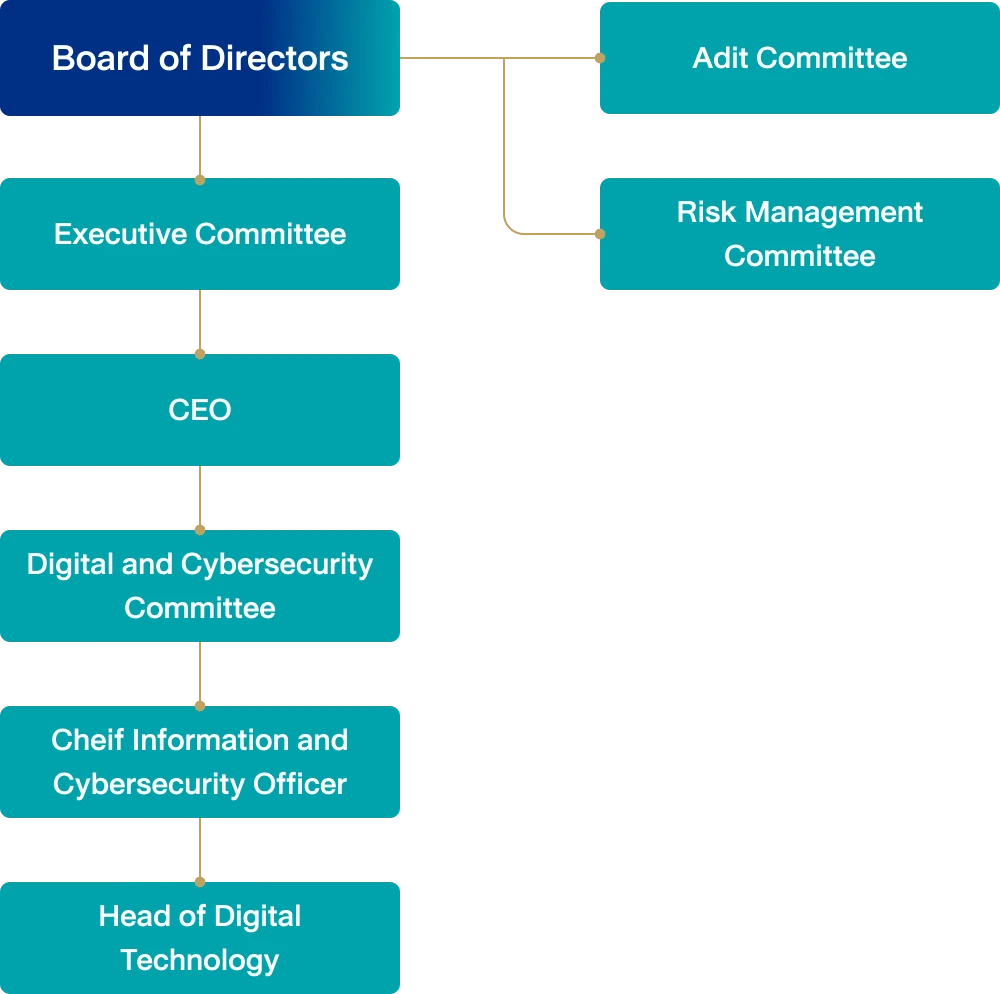
Osotspa’s Digital and Cybersecurity Committee
Osotspa has established a robust cybersecurity governance structure. This structure involves the active participation of the Board of Directors and the Executive Committee in providing strategic direction. Our CEO leads the implementation of cybersecurity policies that are intricately aligned with our sustainable business objectives. We have formed the Digital and Cybersecurity Committee, with Chief Supply Chain and Digital Officer also serving as the Chief Information and Cybersecurity Officer, to ensure efficient operational management.
To further strengthen our approach, we maintain regular communication channels between these governance bodies and the Risk Management Committee (RMC). Furthermore, we prioritize reporting cybersecurity status and pertinent findings to the RMC, recognizing cybersecurity as a critical corporate risk that necessitates vigilant oversight and mitigation efforts, all in accordance with our sustainability goals.

Information Security Policy
Osotspa has implemented a comprehensive IT policy to effectively manage and oversee various aspects of information technology security within the organization. This policy serves as a guiding framework to ensure the confidentiality, integrity, and availability of IT resources, as well as to mitigate potential risks and threats. Through this policy, Osotspa aims to uphold the highest standards of IT security practices, thereby safeguarding sensitive data, protecting against cyberattacks, and maintaining the overall resilience of its IT infrastructure.
Our Information security policy is internally available to all employees via OSP Life application and Internal Corporate Mail.
Osotspa Cybersecurity Roadmap Toward 2025
Osotspa remains committed to fortifying its cybersecurity infrastructure to ensure the safety and integrity of our operations. Safeguarding our digital assets and data is paramount to sustaining our competitive edge and preserving customer trust. Over the years, Osotspa has implemented comprehensive cybersecurity initiatives to mitigate risks and adapt to evolving threats. Looking ahead to 2025, we recognize the increasing importance of bolstering our defenses to stay ahead of cyber adversaries. Our strategic roadmap for cybersecurity encompasses several key areas:
Osotspa has implemented multi-factor authentication across critical systems and applications, adding an extra layer of security beyond traditional passwords. This helped prevent unauthorized access even in the event of password compromise.
The infrastructure of Osotspa is regularly inspected and updated to ensure compliance with industry best practices, including intrusion detection systems, email security, and encryption.
Osotspa prioritizes the security of cloud-native applications by implementing robust security measures tailored to the cloud environment, including rigorous testing, monitoring, and strict access controls.
Osotspa recognizes that human error remains a significant cybersecurity risk. Therefore, Osotspa prioritizes continuous education and training for employees. Regular cybersecurity awareness programs help ensure that employees have the necessary knowledge and skills to handle cyber threats effectively.
Osotspa regularly conducts phishing simulations to assess and improve employees’ knowledge and resilience against phishing attacks. These simulations mimic real-world phishing scenarios, allowing us to identify vulnerabilities and provide targeted training to effectively reduce risks.
Osotspa regularly conducts risk assessments and penetration testing to identify and address potential vulnerabilities in its data and network security systems. By simulating various penetration scenarios, we gain a better understanding and can enhance our defenses, effectively reducing the risk of data breaches.
Osotspa has a comprehensive incident response plan to quickly and effectively mitigate the impact of security incidents. Our response team is regularly simulated and drilled to ensure readiness in the event of a cyber incident, minimizing business operation disruptions.
Osotspa has developed a comprehensive disaster recovery plan to ensure business continuity in the event of natural disasters or other unexpected disruptions. These plans include backup strategies, data recovery procedures, and failover mechanisms to minimize downtime and mitigate the impact of adverse events. The recovery plans are tested semi-annually to verify their effectiveness and identify areas for improvement.
As part of Osotspa’s commitment to end-to-end security, Osotspa closely collaborates with partners and allies to maintain cybersecurity standards throughout the supply chain. Regular assessments are conducted to evaluate third-party providers and enforce compliance with Osotspa’s security requirements.
Osotspa conducts annual risk assessments through both internal and external audits to evaluate operational effectiveness. These assessments provide insights into emerging threats and areas for improvement in the security system, guiding the enhancement of cybersecurity measures.
Company Process for Potential Information Security Incidents:
There are seven steps for identifying and managing actual or potential Information Security Incidents within the Company:
- The Company has a clear and documented incident management process.
- The Company’s IT security system is regularly assessed according to the plan.
- The Digitization department serves as the point of contact and is responsible for ensuring the escalation process is followed.
- Employees encountering actual or potential IT security threats must report to their supervisor and the Digitization department.
- The Digitization department collects, analyzes, and stores evidence as soon as it is reported, while the IT Services sub-function assists the employee in recovering from any damage in parallel.
- All actions taken throughout the process are recorded and stored in written format.
- The IT security incident report is included in the system and process improvement study conducted after the case is closed.
Targets
| Description | 2024 Performance | Long-term Target(2025) |
|---|---|---|
| Data breaches | 0 | 0 |
| Total number of clients, customers, and employees affected by the breaches | 0 | 0 |